Which means 1Password can retailer your entire passwords along with the codes you’d differently obtain, both by way of SMS or an authenticator app corresponding to Authy or Google Authenticator. When you use 1Password to generate one-time passwords (OTPs), you’ll acquire so much in relation to comfort. Authy belongs to 'Security' category of the tech stack, while LastPass can be primarily classified under 'Password Management'. Some of the features offered by Authy are: Very secure- We take security seriously. We use industry standard secure algorithms (HMAC RFC 4426) and 256 bits keys which are always encrypted at rest. Transition procedure with Authy on 1Password The first thing you need to verify that you are using the latest version of 1Password, which support 2FA. On the Mac is the latest version 5.3 for iOS - at least version 5.2, released a couple of months ago.
- Authy 1password Chrome Extension
- Authy 1password App
- Authy 1password
- Authy 1password Or Lastpass Authenticator
- 1Password is an app built to help you keep your online accounts secure. Followed by a six-digit code that's either sent via text message to your phone or accessed through an app such as Authy.
- Sign in to your account on 1Password.com. Select the Login item for the website and click Edit. Click “label” in a new section, and enter “One-time password”. Click to the right of the field and choose One-Time Password.
- Open and unlock 1Password, select the Login item for the website, then click Edit.
- Click the item detail menu to the right of a new field and choose One-Time Password.
- Click to open the QR code scanner window.
- Drag the QR code from the website to the scanner window.
If you can’t drag the QR code, most sites will give you a string of characters you can copy and paste instead.
- Click Save.
- Open and unlock 1Password, select the Login item for the website, then tap Edit.
- Tap “Add new one-time password”.
- Tap to scan the QR code from another device.
If you can’t scan the QR code, most sites will give you a string of characters you can copy and paste instead.
- Tap Done.
Tip
To automatically copy one-time passwords to the clipboard after filling a login, tap Settings > Password AutoFill and turn on Auto-Copy One-Time Passwords.
- Open and unlock 1Password, select the Login item for the website, then select Edit.
- Select to the right of the field (Shift + Enter) and choose One-Time Password.
- Click and choose “From my screen” to scan the QR code.
If you can’t scan the QR code, make sure it’s visible when you minimize 1Password. Alternatively, most sites will give you a string of characters you can copy and paste instead.
- Select Save.
- Open and unlock 1Password, select the Login item for the website, then tap .
- Tap “Add new section”, then tap “Add new field” and choose One-Time Password from the list.
- Tap to scan the QR code from another device.
If you can’t scan the QR code, most sites will give you a string of characters you can copy and paste instead.
- Tap Save.
Tip
To automatically copy one-time passwords to the clipboard after filling a login, tap Settings > Filling and turn on “Auto-copy one-time passwords”.
First up, a note: exporting your Authy tokens presents a security risk, especially if you save them to a file. Anyone that is able to view the tokens can then create the codes needed to access the associated accounts. So… use your head and be safe. With that out of the way:
I’ve recently become very frustrated at the major second-factor authentication (2FA) apps, particularly around the lack of features needed to manage a large number of tokens.
In the security industry, the guideline has long been “use a second factor” mechanism — giving rise to mantras like “something you have and something you know”, which is really the point. However, currently, nearly nobody uses 2FA strictly in that manner: most folks view 2FA as “a second password” mechanism. One they choose, one is based on whatever (generally a seed that’s based on time — the first ‘T’ in TOTP). While that defeats some of the intent behind 2FA, in practice that’s actually probably just fine.

So: as an industry we push vendors and developers to require 2FA. Good news! Many of them are starting to. Herein comes the problem: users now have to manage a lot of tokens. In fact, they have to manage at least one for each app they use.
Authy 1password Chrome Extension
So what’s the big deal? NONE of the major apps used for 2FA (Authy, 1Password, Duo, Google Authenticator, LastPass, etc.) really provide a useful way to manage a large number of accounts:
- Users can’t rename them based on what they want to call them (most of the apps use a combination of the Seed Provider name + username to refer to them. That may be OK with a small number of accounts, but wait until you have 15 “Google” accounts and need to figure out which one is which but you can only see the first 2 or 3 chars of what comes after “Google” on the screen…)
- Tagging doesn’t exist in this world
- Neither does sorting, for most of them
- In some of them, you can’t delete accounts without having to wait at least 24 hours.
- There’s no such thing as export
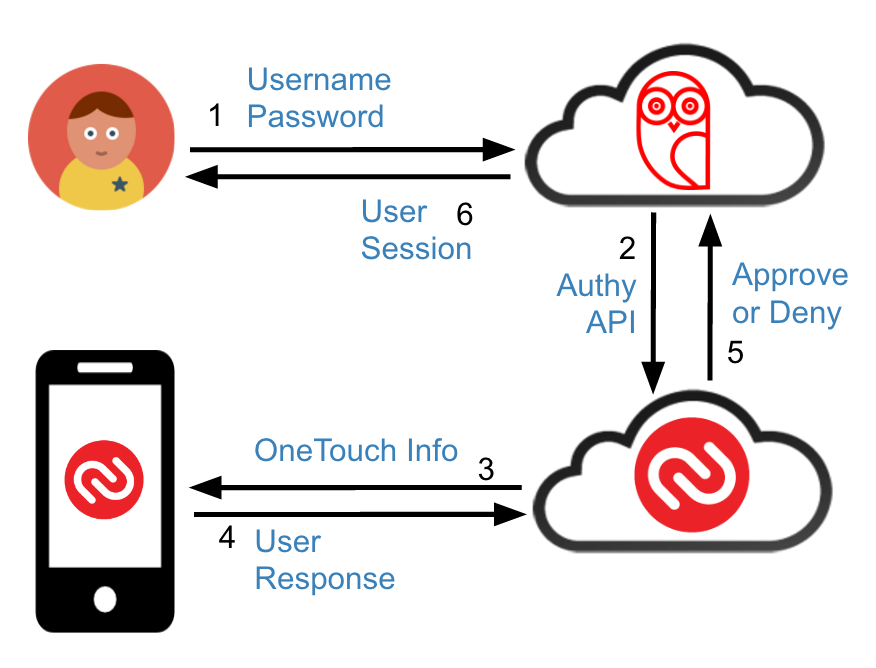
Authy 1password App
Now, some of those have good security reasons behind them (well… OK. Just one, really. The one that most applies to this post: lack of export). Why can’t you export from these apps? Simple: allowing export breaks the 2FA model of “something you have, something you know”. If you can get a dump of seeds, that becomes two things you know, since the device is no longer required. Except… for day to day use, nearly everyone is totally fine with 2FA just being 2 pieces of information that you know. Not to mention: what happens if a software company goes away? Do I lose access to my accounts because I can’t access the tokens anymore? Pretty much zero app developers allow someone that has already configured 2FA to display a scannable QR code (or even just get the seed) once the initial configuration is complete (which, again, is in harmony with good “something you have” mode, but contrary to “good user interface” requirements).

Authy 1password
So… if you are one of those that wants to dump your tokens out of an existing app you are using — and if that app happens to be Authy — you are in luck! It turns out you can do this. It just isn’t super straight foward.
- Open the Authy application, such that you are viewing the accounts you have saved
- Open your browser extensions manager. In Chrome, this can be done by going to chrome://extensions
- In the extensions manager, click “Developer Mode” on the top right
- Find the Authy application (note: this is different than the Authy extension. It should be at the bottom of the page in the “Chrome Apps” section)
- You should see a bit that says “Inspect Views”. It may say “background page, 1 more”. Click the link, until you see “main.html”.
- Click “main.html”, and the Chrome developer tools window should open
- Open the Console (this is the Javascript Console)
- Paste the codeblock below into the console window
- Enjoy your list of accounts. (I recommend doing something like right clicking on the console and “save as” to export the data to a file — but please understand you do this at your own risk, as anyone that is able to access the file can then create a 2FA token for the accounts in the list).
Authy 1password Or Lastpass Authenticator
Here’s the code to paste in step 8 (hat tip to gboudreau and nmurthy):
